BUSINESS
Future-Proofing Business Networks for the Hybrid Workforce
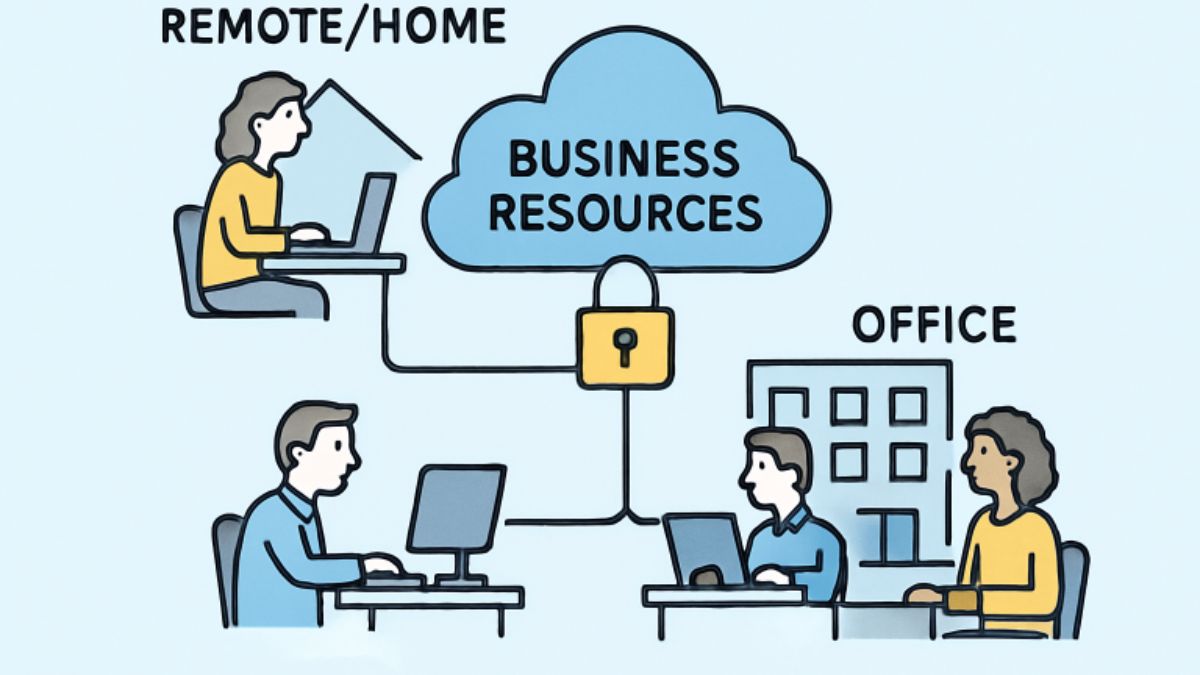
The evolution of hybrid work has completely redefined operational norms for businesses worldwide. Organizations across various industries are seeking a careful balance between flexibility and productivity, as employees now expect the freedom to work from more than just the office. The infrastructure supporting the hybrid workforce must therefore become more robust and adaptable than ever before, enabling seamless transitions between remote and in-office work. As the lines between traditional workspaces and home offices blur, companies face the dual challenge of integrating employees working across multiple locations while maintaining network reliability, performance, and—crucially—security. Understanding what is SASE? has become a pivotal step in safeguarding and optimizing modern business networks, ensuring both continuity and safety.
Establishing a network capable of withstanding new and emerging connectivity challenges requires the adoption of advanced technologies, but also demands a profound reimagining of security, user experience, and scalability principles. Businesses need to move beyond traditional methods and adopt dynamic strategies that adapt to the evolving needs of their workforce. By making smart investments in both technology and operational processes, organizations position themselves to remain competitive and resilient in a rapidly changing and digitized world. With these foundational shifts, enterprises can meet both present challenges and future demands efficiently.
Understanding the Hybrid Workforce
The hybrid workforce represents a blend of remote and on-site employees, creating dynamic and agile business operations. These modern work arrangements, driven by technological advances and shifting employee expectations, can foster improved work-life balance while also enhancing overall productivity. With staff members connecting from diverse settings—be it from their living rooms, coworking spaces, or the office—the conventional constraints of workplace geography are rapidly fading. However, this geographically dispersed configuration introduces new complexities regarding consistent connectivity, real-time communication, and secure access to critical business resources from any location.
For businesses, securing seamless collaboration and productivity requires crafting network environments explicitly designed to handle multiple modes of work. Systems must enable rapid access to both cloud-based assets and sensitive internal systems, all while upholding strict information security and compliance standards. Ensuring that every employee enjoys a reliable, secure, and intuitive digital experience is crucial for maximizing the benefits of a hybrid work model and retaining top talent in a competitive market.
Key Challenges in Hybrid Networking
As businesses embrace hybrid work, they encounter a unique set of obstacles in sustaining cohesive and efficient digital operations:
- Security Risks: The proliferation of devices and endpoints outside traditional workplace perimeters significantly increases the company’s vulnerability to cyber threats, including phishing, ransomware, malware, and unauthorized data access. Keeping every device and connection secure, regardless of location, is more challenging than ever.
- Connectivity Issues: Remote employees often rely on inconsistent and sometimes unreliable network qualities at home, in coffee shops, or public hubs, which can degrade both performance and user experience. Network outages or slow speeds can disrupt critical workflows, hampering productivity.
- Resource Management: Balancing workloads and allocating network bandwidth for business-critical applications requires ongoing oversight, particularly as usage fluctuates throughout a typical workday. IT teams must continuously manage resources to prevent bottlenecks and ensure mission-critical applications remain accessible.
Without proper planning and proactive measures, these challenges can lead to operational inefficiencies, employee frustration, and in the worst case, compromise of sensitive corporate data. Companies must adopt a holistic approach to overcome these hurdles, integrating technical and managerial solutions to safeguard both users and assets.
Implementing Advanced Network Technologies
Leading organizations are combating hybrid networking challenges by deploying next-generation technologies specifically designed to deliver the speed, scale, and flexibility required for today’s dynamic work environment:
- Wi-Fi 6E: This advanced wireless standard expands the available spectrum, reducing device congestion and supporting a new generation of high-bandwidth business applications. With lower latency and substantially increased capacity, Wi-Fi 6E enables uninterrupted collaboration and faster data transfers, especially as growing device counts strain older networks for more on the business benefits and adoption of Wi-Fi 6E.
- 5G Integration: The rollout of 5G networks grants businesses access to wireless connections with ultra-fast speeds and minimal lag. This breakthrough benefits not only mobile and field workers but also improves the experience in underserved office locations. As 5G continues to expand, enterprises gain the bandwidth and reliability previously only possible with wired connections.
Enhancing Security Measures
Security must remain at the forefront when transitioning to hybrid architectures. As network perimeters become increasingly porous, businesses require multi-layered, adaptive defenses to protect data and users, no matter where work is being done:
- Zero Trust Network Access (ZTNA): ZTNA reimagines traditional trust models by enforcing authentication and authorization for every user and device at every login attempt. By abandoning the notion of implicit trust within the network, ZTNA helps prevent attackers from moving laterally even if they breach one endpoint.
- Secure Access Service Edge (SASE): SASE unifies networking and security solutions in the cloud, enabling decentralized, policy-driven control and consistent protection across all devices. By centralizing policy management, SASE eliminates security silos and closes protection gaps, empowering businesses to manage large, distributed workforces securely.
With cyberattacks growing in both frequency and sophistication, leveraging solutions that continuously validate and authenticate every user and connection is more than a trend—it’s a necessity.
Prioritizing User Experience
The ultimate success of a hybrid workforce depends on employees being able to work efficiently, regardless of their location. Addressing the user experience not only keeps teams productive, but also encourages engagement and reduces turnover:
- Unified Communication Tools: Integrated platforms offer secure chat, video conferencing, document collaboration, and file sharing in a single interface. These tools remove friction from workflows, make teamwork intuitive, and help employees maintain strong interpersonal connections, even remotely.
- Performance Monitoring: The adoption of real-time monitoring tools enables IT teams to track network health, quickly identify performance issues, and proactively address bottlenecks. Well-monitored networks foster a smoother, higher-quality work experience by minimizing downtime and ensuring accessibility issues are resolved.
When businesses make seamless digital collaboration a cornerstone, they create environments where employees can focus on contributing their best, no matter their physical location.
Investing in Scalable Infrastructure
A future-ready network must be able to evolve in tandem with business growth, changing use cases, and shifting workforce dynamics. Building in this flexibility is crucial for reducing disruptions and establishing a strong foundation for continued success:
- Cloud-Based Services: Adopting cloud platforms enables organizations to rapidly scale application deployments and resource utilization, thereby lowering upfront capital expenditures and simplifying management. Cloud infrastructure offers powerful agility and supports global operations by making data and applications available from any location, at any time.
- Modular Hardware: Deploying modular, easily upgradable network hardware enables organizations to expand their digital infrastructure incrementally, allowing for seamless growth. Rather than overinvesting in capacity, businesses can align their spending with growth, maintaining performance without incurring unnecessary expenses.
Continuous Monitoring and Optimization
Building a resilient hybrid network demands more than simply installing the right equipment and tools at the outset. Ongoing monitoring, analysis, and intelligent automation help organizations stay aligned with fluctuating business demands, emerging threats, and evolving work patterns:
- Network Analytics: Leveraging analytics to analyze network traffic and monitor real-time user patterns enables organizations to identify bottlenecks, forecast future requirements, and take preemptive action to avoid service interruptions or performance dips.
- Automated Management: Intelligent automation technologies permit dynamic resource allocation, load balancing, and rapid response to changes in workforce activity. Automation substantially reduces manual intervention, speeds up incident responses, and ensures networks adapt in real-time.
This continuous feedback loop ensures the network remains not only functional but also highly optimized for the needs of both the business and its users.
Conclusion
Meeting the demands of a hybrid workforce requires strategic investments across technology, security, and user-centric processes. By adopting advanced solutions such as Wi-Fi 6E, 5G, and SASE, alongside rigorous monitoring and a scalable, modular infrastructure, companies can ensure their networks remain resilient, secure, and fully prepared for the demands of the modern era. These steps are fundamental to ensuring operational continuity and empowering organizations to thrive as the very nature of work continues to evolve.
BUSINESS
How Cloud-Based POS Systems Differ From Traditional POS

Restaurant POS systems have evolved significantly over the past decade. What was once a simple cash register with local software has become a connected platform that manages transactions, reporting, menus, and integrations across multiple channels.
Understanding the differences between cloud-based and traditional POS systems helps restaurant operators make more informed technology decisions especially when planning for growth or operational efficiency.
Where Traditional POS Systems Store Data
Traditional POS systems typically rely on on-site servers installed inside the restaurant. These servers store transaction data, menu configurations, and reporting information locally. Terminals connect directly to that internal server to process sales.
While this setup can function reliably in single-location environments, it comes with limitations. Updates often require manual installation. Reporting access may be limited to on-site devices. Adding new locations usually means installing separate servers at each store.
If the local server experiences hardware issues, the entire system can be affected. Maintenance and troubleshooting often require in-person IT support.
How Cloud Architecture Changes The Model
A cloud based pos shifts data storage and processing to secure remote servers rather than relying solely on hardware inside the restaurant. Terminals and devices connect to the cloud through the internet, syncing transactions and updates continuously.
This centralized structure offers several advantages. Reporting dashboards can be accessed remotely. Menu updates can be deployed across locations instantly. Software updates are handled centrally instead of manually at each store.
For multi-unit operators, this architecture makes scaling much simpler. Instead of building separate infrastructure for every new location, additional stores connect to the same centralized system.
Real-Time Data And Visibility
One of the biggest differences between cloud and traditional POS systems is data visibility.
In traditional setups, reporting may depend on exporting files or manually syncing data between systems. Delays are common, especially in multi-location operations.
Cloud systems sync data in near real time. When a transaction occurs at one location, the data updates centrally. Leadership teams can monitor performance across stores without waiting for end-of-day uploads.
This real-time visibility supports faster decision-making, particularly during promotions or peak service periods.
Integration With Kitchen Systems
Modern restaurants rely heavily on digital kitchen workflows. The ability to integrate seamlessly with a kds system is another key difference between cloud and traditional platforms.
Cloud-based systems often provide smoother integration with kitchen displays because they operate within a centralized environment. Orders entered at the POS sync instantly with kitchen screens, and menu updates reflect automatically across all connected devices.
Traditional systems can also integrate with kitchen displays, but updates may require local configuration at each store. This increases the risk of inconsistencies over time.
Supporting Multi-Channel Service
Restaurants today serve guests through multiple channels: dine-in, online ordering, takeout, and drive-thru. Managing these channels through disconnected systems creates complexity.
Cloud POS platforms are generally designed to unify these workflows under one system. For example, integration with a drive thru headset system can be handled within the same centralized environment. Orders taken in the drive-thru feed directly into the POS, kitchen workflow, and reporting dashboard.
Traditional systems may require additional configuration or separate reporting tools to manage these channels effectively.
Maintenance And Updates
Traditional POS systems require manual software updates. Each location may need to install patches individually. If updates are missed or delayed, inconsistencies can appear across stores.
Cloud-based systems typically receive automatic updates deployed centrally by the provider. This ensures that all locations are running the same version of the software without additional effort from store-level staff.
Security Differences
Security practices also differ between the two models. In traditional setups, the restaurant is often responsible for maintaining server security, applying patches, and managing backups.
Cloud-based platforms usually include centralized security management, encryption protocols, and automatic updates. Because updates are handled at the provider level, vulnerabilities can be addressed more quickly across all locations.
Restaurants still need to follow best practices for passwords and network security, but cloud architecture often reduces exposure related to outdated local systems.
Scalability And Growth
With traditional POS systems, opening a new location often requires installing a new server and configuring systems independently. Reporting consolidation can become complicated.
Cloud-based systems allow new locations to connect to the existing infrastructure. Menus, pricing templates, and user permissions can be replicated quickly. This makes expansion faster and more standardized.
For restaurant brands planning multi-location growth, this scalability is a major advantage.
Offline Considerations
A common perception is that traditional systems are more reliable because they operate locally. However, many modern cloud POS platforms include offline capabilities that allow transactions to continue temporarily during internet disruptions.
Once connectivity is restored, stored data syncs back to the cloud. This offers a balance between centralized control and operational resilience.
Final Thoughts
Cloud-based POS systems differ from traditional POS platforms in how they store data, sync information, manage updates, and support multi-location operations. While traditional systems rely on local servers and manual maintenance, cloud architecture centralizes data, enables real-time visibility, and simplifies scalability. With integrated kitchen and drive-thru support, cloud POS platforms provide a more flexible and connected foundation for modern restaurants. For operators planning long-term growth and operational visibility, understanding these differences is essential before choosing a system.
BUSINESS
How Everyday Investors Can Spot Red Flags in Financial Markets

Investing offers a unique pathway to growing wealth and achieving long-term financial stability, but the same financial markets that generate opportunity are also riddled with risks that can challenge even the most experienced investor. The complex and highly dynamic nature of today’s investing landscape means it’s crucial for individuals, especially those without the backing of institutional analysis teams, to stay aware of potential pitfalls and manipulative schemes. Spotting red flags early not only allows you to protect your capital but also positions you to make more informed, rational financial decisions for your future. When confusion or suspicion arises about a potential investment, reaching out to a California securities fraud lawyer brings legal insight and advocacy that can be invaluable in addressing uncertainties or pursuing remedies.
Education is an investor’s most powerful tool, whether you’re just starting out or have years of experience navigating stocks, bonds, or newer assets like cryptocurrencies. The more you understand about the mechanisms behind investments and the tactics scammers use, the more confidently you can proceed. Many bad actors exploit lapses in investor knowledge and leverage urgency or fear of missing out for profit. By continually seeking trustworthy guidance, understanding regulatory frameworks, and investing in your own financial literacy, you strengthen your ability to spot danger before it turns into a loss. Embracing a mindset of skepticism balanced with learning is the foundation of a healthy, long-term investment practice.
Understanding Investment Red Flags
Red flags in financial markets are warning signals that something may be amiss with a particular investment opportunity. These aren’t always overt signs of fraud; sometimes they are subtle clues buried in complicated sales pitches or ambiguous disclosure documents. A red flag might represent anything from the risk of outright fraud to simply a disadvantageous deal presented in a misleadingly attractive way. For most retail investors, recognizing these signs early is essential in minimizing the potential for considerable financial loss and emotional stress. Regularly consulting resources such as the U.S. Securities and Exchange Commission’s published alerts on fraudulent activity can greatly improve your ability to distinguish a sound investment from a potential scam.
Investment fraud appears in various forms. For example, Ponzi and pyramid schemes often lure victims with promises of high, steady returns with no apparent risk, making such opportunities seem “fail-proof.” Alternatively, some schemes involve misleading representations that obscure the true risks or inflate the potential rewards well beyond realistic outcomes. As technology evolves, new vehicles such as speculative cryptocurrencies or unregulated online lending platforms create fresh avenues for deception, often appealing to investors’ curiosity and desire for innovation. Scammers can be persuasive and skilled at psychological manipulation, using sophisticated narratives to earn your trust or pressure you into acting quickly before you have time to think. In these situations, a healthy level of skepticism and a knowledge of common red flags can shield you from devastating losses.
Common Warning Signs
- Guaranteed Returns: No credible investment opportunity can legally promise high, fixed, or guaranteed returns. Investments inherently involve some level of risk, and the possibility of loss is what enables the potential for reward. Claims of steady profits, especially those that seem abnormally high relative to market rates, are red flags for fraud or extremely risky undertakings.
- Unsolicited Offers: Investment invitations that land out of the blue, particularly from individuals or organizations unknown to you, should never be accepted without rigorous vetting. These might come in the form of cold calls, unsolicited emails, or social media messages. Many investment scams, especially those originating overseas, begin with unexpected outreach and the promise of exclusive opportunities.
- Pressure to Act Quickly: Urgency is frequently deployed by fraudsters to prevent potential victims from doing their homework. If someone tells you an opportunity is time-sensitive or must be seized immediately to avoid missing out, slow down. Taking the time to independently verify details is a critical aspect of smart investing—and any reluctance to provide you with that time should raise suspicion.
- Unregistered Products: Before you invest, confirm that both the product and the salesperson are registered with the SEC, FINRA, or your state’s securities regulator. Registration requirements exist to create transparency, and legitimate investments will always have a paper trail you can follow and review. Unregistered or offshore investments are much harder to recover if something goes wrong.
- Complex Strategies: Many scams thrive in opacity. If you cannot easily understand or explain how a proposed investment works to a friend or family member, it’s a sign that either the structure is unnecessarily complicated or details are being deliberately obscured. Complicated language or technical jargon may be used to intimidate or confuse you into silent agreement.
Strategies for Identifying Red Flags
- Conduct Thorough Research: No matter how promising an opportunity appears, always research the company, product, or individual proposing it. Review financial statements, the business’s regulatory standing, and recent news. Trusted financial news outlets can offer insight into public companies, while official court or government filings provide details on legal history and leadership reputation.
- Verify Credentials: Use regulatory agency tools, such as FINRA’s BrokerCheck or the SEC’s database, to verify licensing and disciplinary history. Credentials prove legitimacy and bolster trust, while inconsistencies or disciplinary flags are reasons to walk away.
- Monitor Financial News: Because financial conditions and reputations can change rapidly, staying up to date is key. Watch for sudden shifts in a company’s standing, leadership shakeups, or regulatory investigations, all of which could signal emerging risks that might not have been visible at the outset.
- Seek Independent Advice: Before committing large sums or entering new types of investments, get a second opinion from a fee-only fiduciary or another financial expert who doesn’t benefit directly from your choice. Independent advisors provide honest feedback and may spot issues you’ve overlooked under sales pressure or emotional attachment.
Resources for Investors
Investing doesn’t have to be a solo venture. Many regulators and consumer advocacy organizations provide easily accessible resources designed to help everyday investors make safe, informed choices. The Financial Industry Regulatory Authority (FINRA) is a prime example, offering step-by-step guidance for spotting investment scams and database searches of broker or firm backgrounds. These resources are constantly updated as scammers develop new tactics.
Beyond regulatory bodies, numerous educational platforms and nonprofit consumer advocates offer tools, online classes, and warnings tailored to different experience levels. Government-sponsored websites focus on investor protection, offering checklists, fraud warnings, and Q&A sections to address common concerns and emerging investment trends. Staying proactive and routinely consulting these resources is essential for maintaining a high level of financial awareness.
Conclusion
Financial markets provide opportunities, but the risks cannot be ignored, especially when scam artists are determined to find new ways to separate you from your money. By staying watchful for warning signs like unregistered products, unsolicited offers, and high-pressure tactics, you significantly reduce your chances of falling victim to fraud. Diligence in researching, using trustworthy resources, and seeking knowledgeable independent opinions is the best way to ensure your investments work for you not against you. If a deal seems suspicious or just too attractive for its own good, pause and look deeper; your caution today can safeguard your financial well-being for years to come.
BUSINESS
What Are Managed Print Services and How Do They Work?
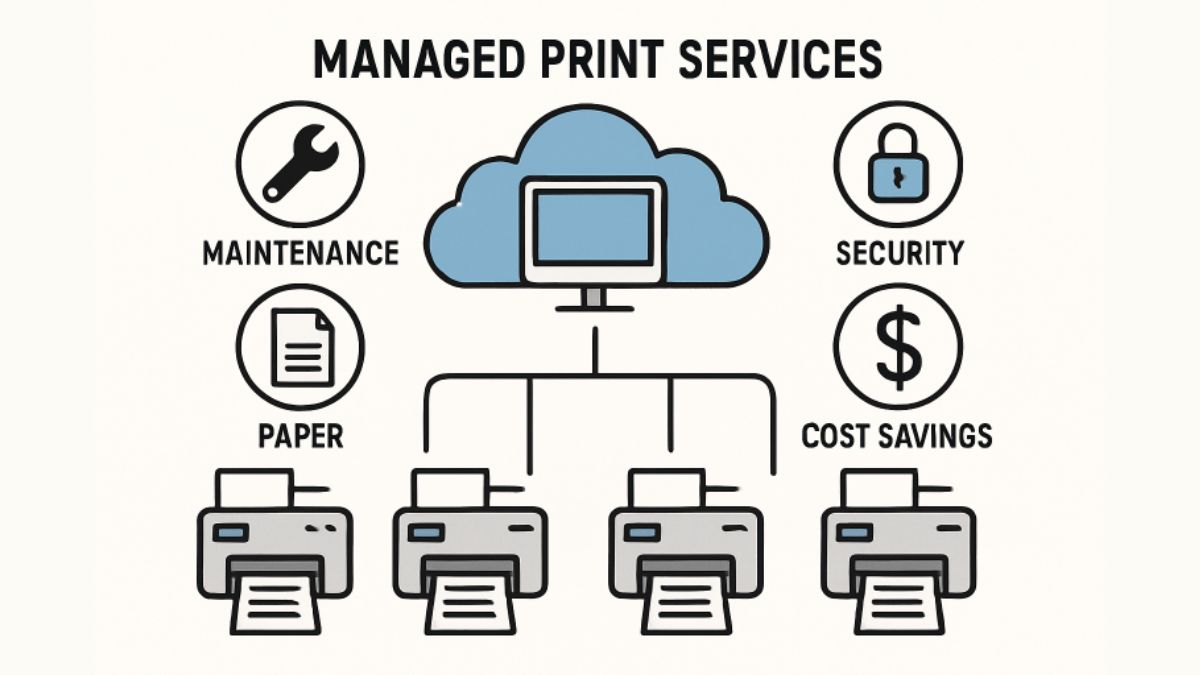
Introduction to Managed Print Services
Managed Print Services (MPS) have become an essential solution for businesses looking to streamline their printing operations, cut unnecessary costs, and enhance information security. By leveraging the expertise of a dedicated provider, organizations can delegate the responsibility for their entire print environment, from routine maintenance to intricate security measures. Companies like Everworx offer tailored MPS solutions for various industries, ensuring devices run smoothly and workflows remain efficient.
Today’s workplaces demand seamless document processing, quick response times to technical issues, and vigilant security protocols. MPS providers can address all these requirements by proactively managing print devices, optimizing consumable inventory, and recommending improvements based on real-time data. This collaborative approach not only delivers immediate operational benefits but also long-term strategic advantages that foster growth and adaptation in an evolving business landscape.
Key Components of Managed Print Services
Implementing an MPS framework involves a series of well-structured steps, each designed to address specific challenges in document management and output. Here are the essential components that form the backbone of any effective MPS deployment:
- Assessment: This foundational phase involves a thorough evaluation of the existing print environment, identifying inefficiencies, redundancies, and opportunities for consolidation or improvement.
- Optimization: After a thorough assessment, MPS providers work with organizations to streamline printer fleets, improve print workflows, and implement cost-reduction strategies without sacrificing quality or security.
- Proactive Maintenance: Ongoing monitoring and routine maintenance help reduce device downtime, extend hardware lifespan, and minimize disruptions for end users.
- Supply Management: Automated supply replenishment systems eliminate the risk of running out of critical consumables like toner or paper while slashing administrative efforts.
- Security Enhancements: With stricter data protection regulations in place, modern MPS solutions offer advanced security features such as user authentication and encrypted document workflows to safeguard sensitive information.
During the optimization phase, some providers introduce technology that tracks print usage, detects patterns, and provides actionable insights. According to CIO.com, leveraging such technology can reveal surprising sources of wastage, including underutilized devices and inefficient paper workflows, that often go unnoticed in informal print environments.
Benefits of Adopting Managed Print Services
By adopting Managed Print Services, organizations across various sectors can derive measurable benefits that touch on financial, operational, and environmental priorities:
- Cost Reduction: MPS-driven insights target and eliminate wasteful practices, enabling businesses to reduce their print budgets significantly. Industry reports have found that some adopters achieve up to a 50% reduction in printing expenditures.
- Enhanced Productivity: With technical issues preemptively managed, employees are freed from troubleshooting printer problems or dealing with supply shortages. This lets staff focus on value-generating activities instead.
- Improved Security: Secure print solutions, including PIN release and secure print queues, significantly reduce the risk of sensitive documents falling into the wrong hands or being inadvertently left on devices.
- Environmental Sustainability: Optimized print infrastructures result in less paper and toner waste and lower energy consumption. MPS providers often guide organizations toward environmentally responsible practices, aligning with broader corporate sustainability objectives.
One of the hidden benefits of MPS is improved document workflow across departments. Modern MPS solutions can integrate with digital document management systems, enabling seamless transitions from paper-based to digital processes. As noted by CIO.com, the move toward digitization not only increases efficiency but can also improve compliance and auditability for regulated industries.
Implementing Managed Print Services in Your Organization
Integrating MPS into your organization is a transformative process that requires careful planning, provider selection, and ongoing measurement to achieve optimal results. The general process includes:
- Conduct a Comprehensive Assessment: Work with your MPS provider to map your current device landscape, analyze print volume and patterns, and document your specific pain points.
- Select a Reputable MPS Provider: Choose a trusted partner with industry experience and the flexibility to design customized solutions. Assess their support capabilities, technology offerings, and security approach.
- Develop a Customized Strategy: Collaboratively devise a plan for device consolidation, policy enforcement, supply management, and future scalability, all tailored to your key business objectives.
- Implement and Monitor: Launch the agreed solution with minimum disruption. Lean on integrated monitoring tools to regularly gauge device health, usage trends, and the solution’s effectiveness against your defined goals.
Real-World Example: Dell Technologies’ Success with MPS
Many top organizations are embracing Managed Print Services (MPS) to optimize operations and reduce costs. For instance, Dell Technologies partnered with a specialized MPS provider to streamline its entire print fleet and automate helpdesk support for printing issues. This transformation led to a remarkable 60% reduction in print-related support tickets, freeing IT teams from routine troubleshooting. As a result, staff could concentrate on higher-value projects, improve overall service delivery, and enhance operational efficiency. MPS adoption demonstrates how strategic print management can drive both productivity and organizational performance.
Conclusion
In today’s fast-moving business environment, Managed Print Services go far beyond simply reducing paper and toner usage. They offer a comprehensive approach to controlling print-related expenses, streamlining workflows, and improving overall operational efficiency. By centralizing device management, automating supply replenishment, and monitoring usage patterns, organizations gain clearer visibility into costs and performance. Managed Print Services also enhances document security through access controls and tracking features while supporting sustainability initiatives through waste reduction. With the right provider and a strategic rollout plan, companies can transform printing into a valuable, well-managed business asset.
-

 TOPIC7 months ago
TOPIC7 months agoSymbols of Hope: The 15th Belenismo sa Tarlac
-

 TOPIC7 months ago
TOPIC7 months ago“The Journey Beyond Fashion” – Ditta Sandico
-

 NEWS7 months ago
NEWS7 months agoHistorical Churches in Manila
-

 TOPIC7 months ago
TOPIC7 months agoRIZAL at 160: a Filipino Feat in Britain
-

 TOPIC7 months ago
TOPIC7 months ago5 Must-Have Products From Adarna House to Nurture Your Roots
-

 TOPIC7 months ago
TOPIC7 months agoBoats with Two Strings
-

 TOPIC7 months ago
TOPIC7 months ago“Recuerdos de Filipinas – Felix Laureano”
-

 TOPIC7 months ago
TOPIC7 months agoFilipino, alternative language course at Moscow State University
